A newly discovered phishing kit targeting PayPal users is trying to steal a large set of personal information from victims that includes government identification documents and photos.
Over 400 million individuals and companies are using PayPal as an online payment solution.
The kit is hosted on legitimate WordPress websites that have been hacked, which allows it to evade detection to a certain degree.
Breaching websites with weak login
Researchers at internet technology company Akamai found the phishing kit after the threat actor planted it on their WordPress honeypot.
The threat actor targets poorly secured websites and brute-forces their log in using a list of common credential pairs found online. They use this access to install a file management plugin that allows uploading the phishing kit to the breached site.
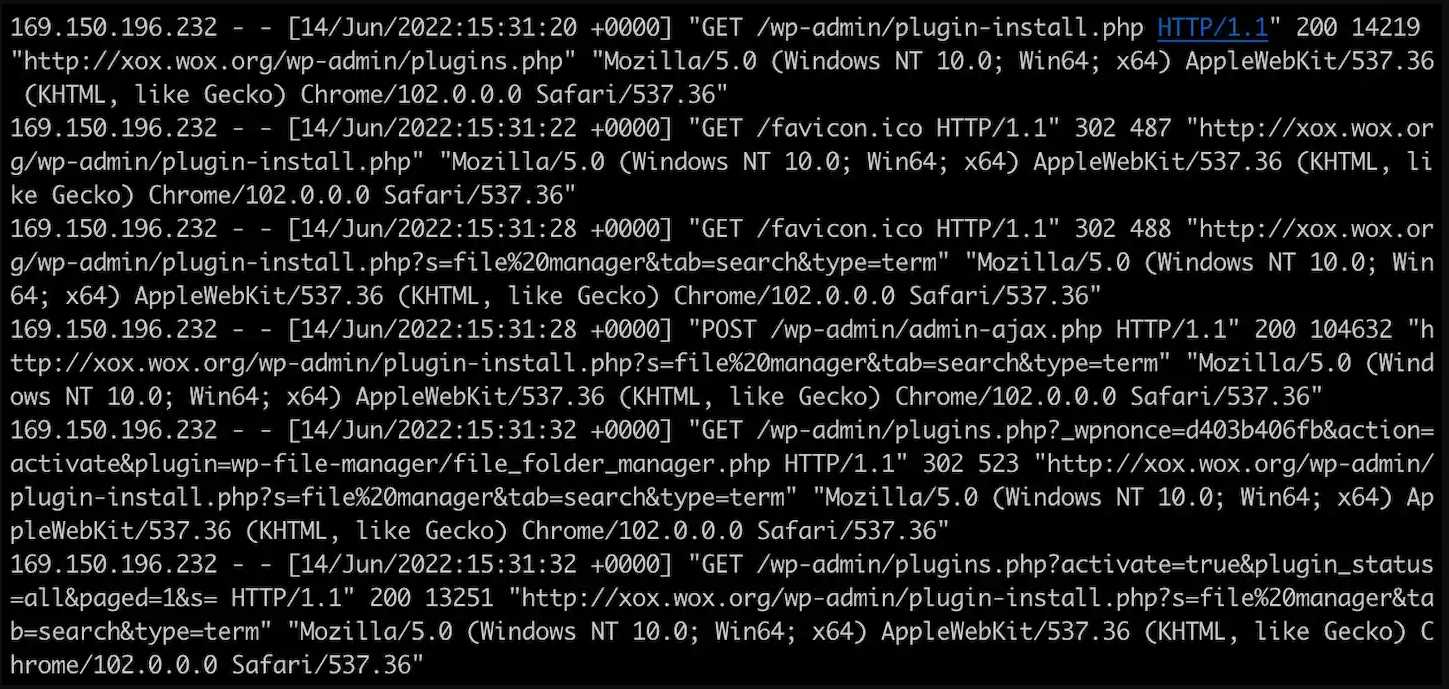
Akamai discovered that one method the phishing kit uses to avoid detection is to cross-reference IP addresses to domains belonging to a specific set of companies, including some orgs in the cybersecurity industry.
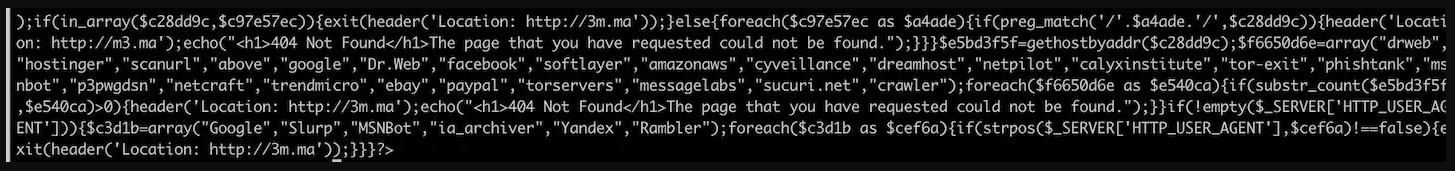
Legit-looking page
The researchers noticed that the author of the phishing kit made an effort to make the fraudulent page look professional and mimic the original PayPal site as much as possible.
One aspect they observed was that the author uses htaccess to rewrite the URL so that it does not end with the extension of the PHP file. This adds to a cleaner, more polished appearance that lends legitimacy.
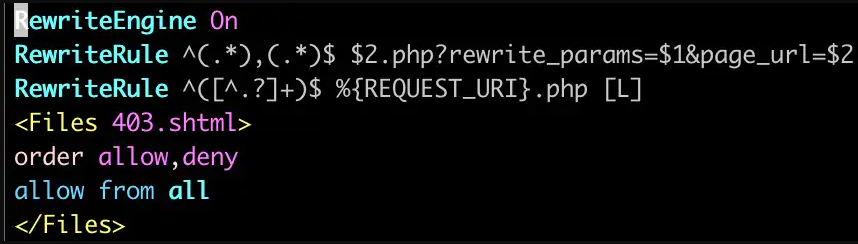
Also, all graphical interface elements in the forms are styled after PayPal’s theme, so the phishing pages have a seemingly authentic appearance.
Data stealing process
Stealing a victim’s personal data starts with presenting them a CAPTCHA challenge, a step that creates a false sense of legitimacy.
.png)
After this stage, the victim is asked to log into their PayPal account using their email address and password, which are automatically delivered to the threat actor.
This is not all, though. Under the pretense of “unusual activity” associated with the victim’s account, the threat actor asks for more verification information.
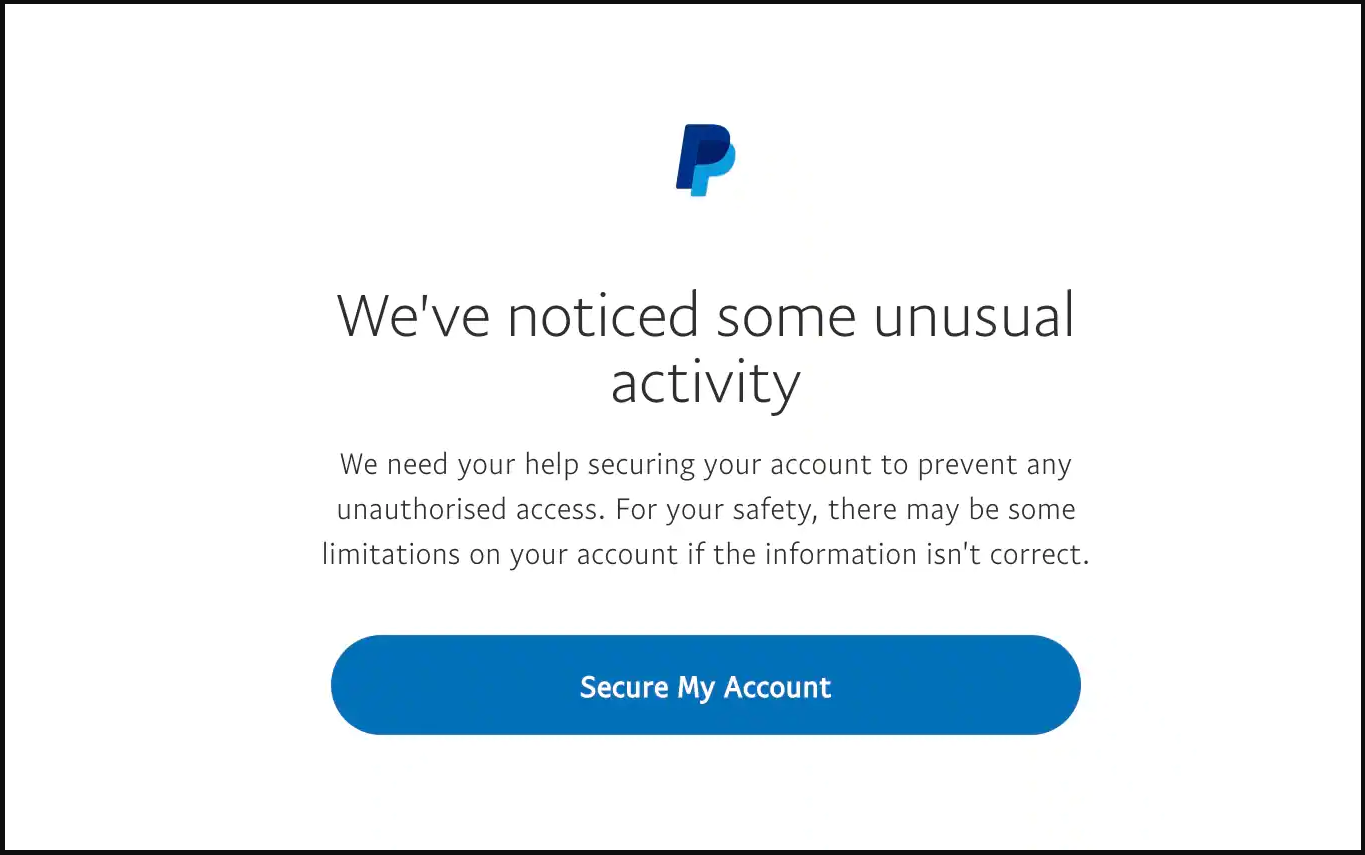
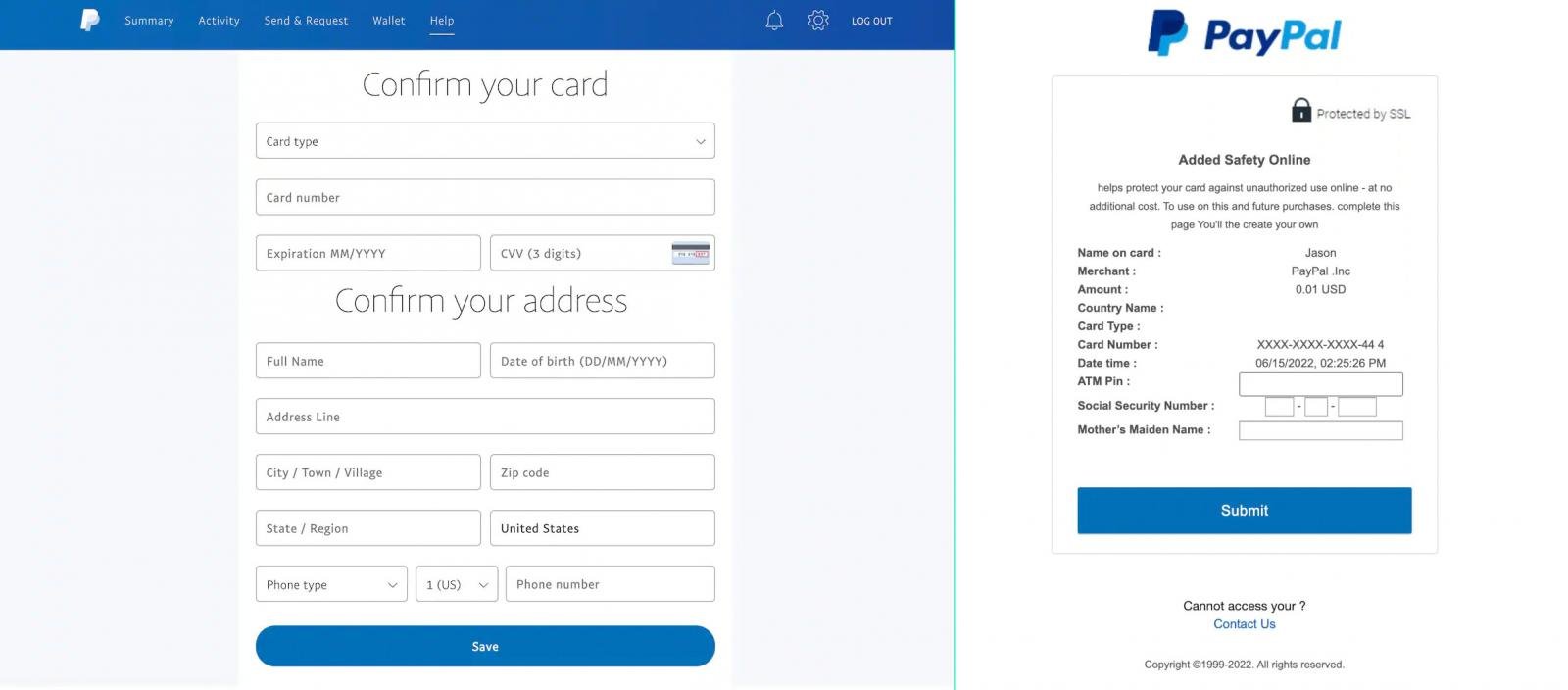
In a subsequent page, the victim is asked to provide a host of personal and financial details that include payment card data along with the card verification code, physical address, social security number, mother’s maiden name.
It appears that the phishing kit was built to squeeze all the personal information from the victim. Apart from the card data typically collected in phishing scams, this one also demands the social security number, mother’s maiden name, and even the card’s PIN number for transactions at ATM machines.
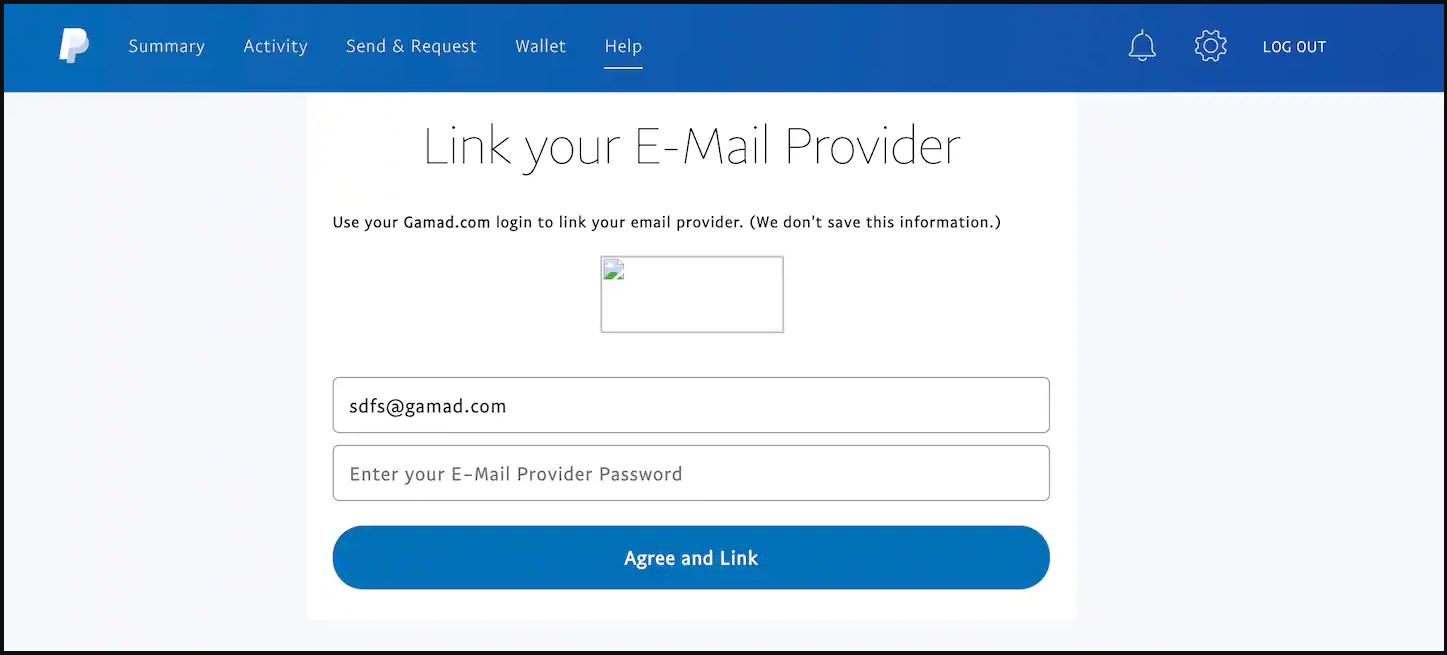
Collecting this much information is not typical to phishing kits. However, this one goes even further and asks victims to link their email account to PayPal. This would give the attacker a token that could be used to access the contents of the provided email address.
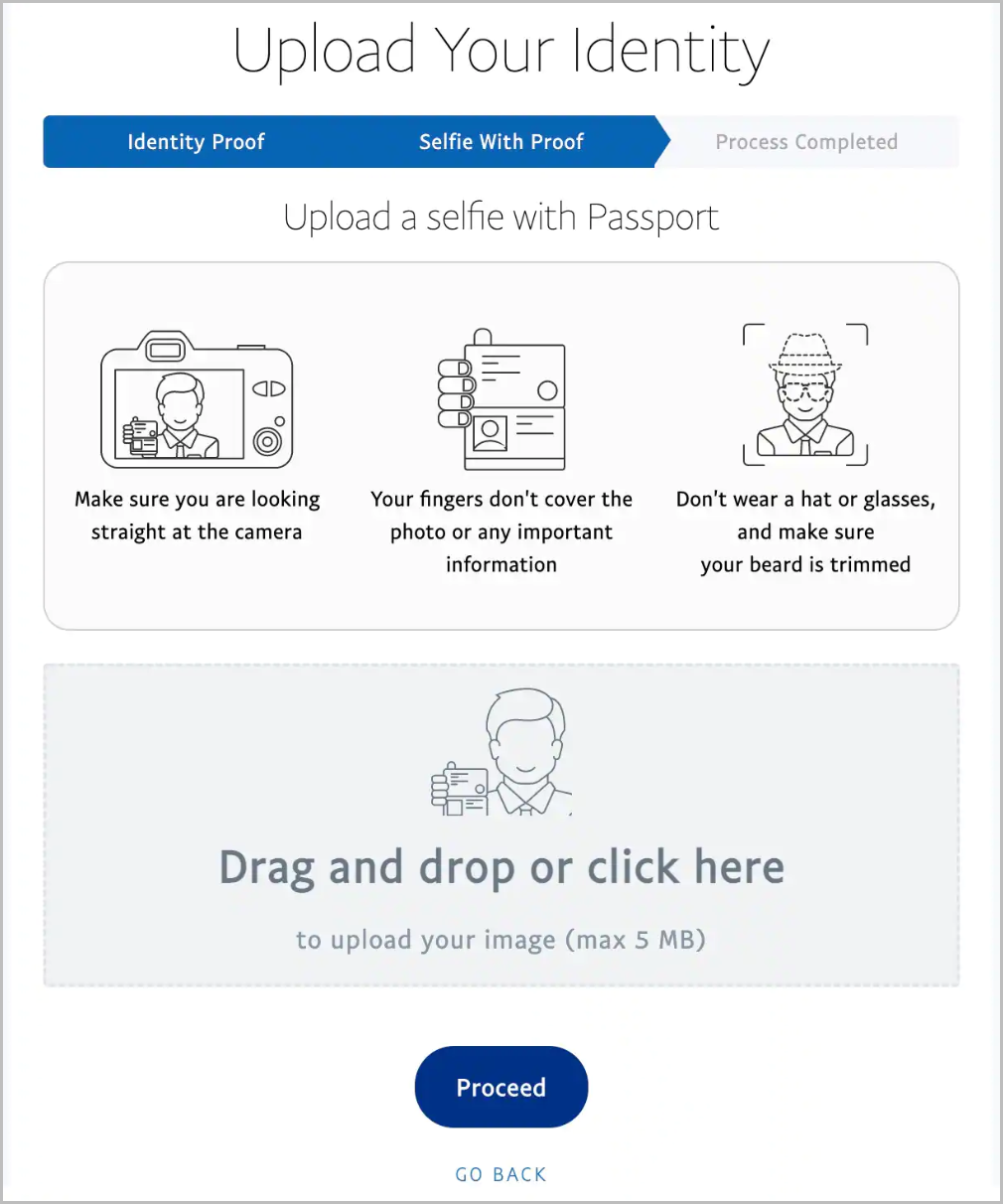
Despite having collected a massive amount of personal information, the threat actor is not finished. In the next step, they ask the victim to upload their official identification documents to confirm their identity.
The accepted documents are passport, national ID, or a driver’s license and the upload procedure comes with specific instructions, just as PayPal or a legitimate service would ask from their users.
Cybercriminals could use all this information for a variety of illegal activities ranging from anything related to identity theft to launder money (e.g. creating cryptocurrency trading accounts, registering companies) and maintaining anonymity when purchasing services to taking over banking accounts or cloning payment cards.
Uploading government documents and taking a selfie to verify them is a bigger ballgame for a victim than just losing credit card information — it could be used to create cryptocurrency trading accounts under the victim’s name. These could then be used to launder money, evade taxes, or provide anonymity for other cybercrimes. – Akamai
Although the phishing kit appears sophisticated, the researchers discovered that its file upload feature comes with a vulnerability that could be exploited to upload a web shell and take control of the compromised website.
Provided the huge amount of information requested, the scam may appear obvious to some users. However, Akamai researchers believe that this specific social engineering element is what makes the kit successful.
They explain that identity verification is normal these days and this can be done in multiple ways. “People judge brands and companies on their security measures these days,” the researchers say.
The use of the captcha challenge signals from the beginning that additional verification may be expected. By using the same methods as legitimate services, the threat actor solidifies the victim’s trust.
Users are advised to check the domain name of a page asking for sensitive information. They can also go to the official page of the service, by typing it manually in the browser, to check if identity verification is in order.




















